“The ICS [Industrial Control System] community, as a whole, does not fully understand the extent of the possibilities available to an attacker. The industry must approach the problem of ICS attacks as they do equipment prognostics. It is not a matter of if it will fail, but when it will fail, and the community must complete the necessary assessment, engineering and instrumentation tasks to plan for and deal with the potential for attacks on the best terms.” 1
From the outside looking in, risk assessment for operational technology (OT) may seem like a relatively straightforward process, but the reality is, it’s extremely difficult to do well.
Think of it like cooking up a Bolognese sauce. There are many ‘recipes’ (i.e. frameworks) and everyone seems to be doing it without a fuss, but if you don’t take the time to prepare your ‘ingredients’ and apply the right amount of care and patience, your ‘sauce’ (i.e. risk assessment) will ultimately be ‘tasteless’ and fail to meet expectations.
When it comes to OT cyber risk assessment, the insights we’ve gleaned at SIS from working with an ever-broadening client base tell us that organisations and consultancies, even specialists, in the critical area of industrial cyber security still have a long way to go before they really get the formula right.
This is an industry-wide phenomenon that takes no prisoners, us included.
What is risk assessment?
Risk assessment is about fully understanding the threats, exploitable weaknesses and potential impacts of your systems being accessed malicious adversaries. For operational technology and industrial control systems, this is more complex than the standard risk assessment for IT. OT has its own unique set of vulnerabilities and considerations that need to be taken into account.
The key equation in risk analysis:
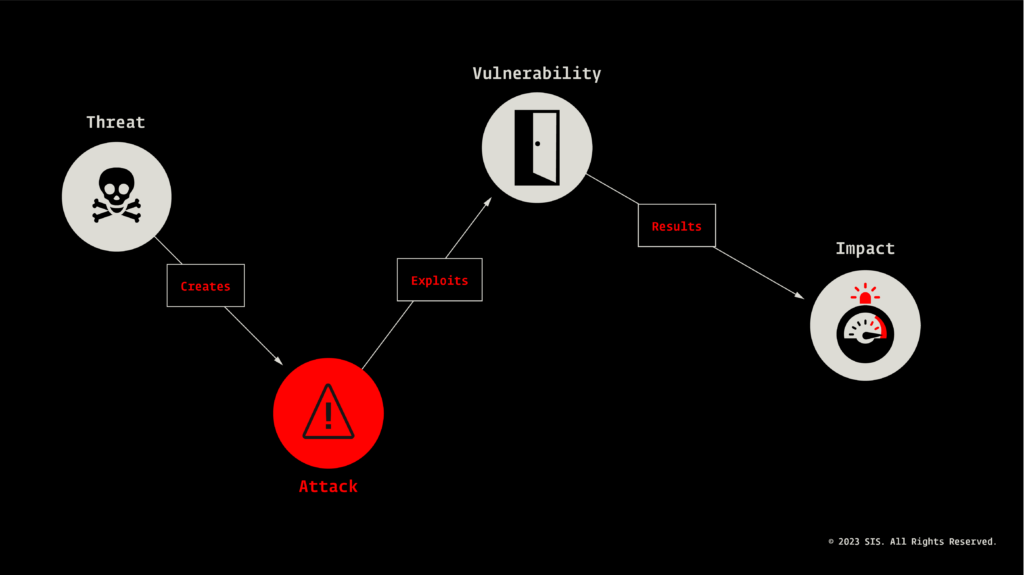
A successful cyber-attack relies on some fundamental ingredients; it requires motivation, it needs intent; and it also needs an individual, or a team, who possess the capabilities and skills to execute the attack by exploiting vulnerabilities.
To understand how an organisation or department is positioned to protect its OT and ICS, the main points of risk assessment are:
- Threats: understanding the kinds of threats your organisation’s OT could be exposed to, and the consequences of a hacker gaining access to your ICS;
- Threat agents: understanding who has the capacity to initiate and carry out a cyber-attack against your business and its OT;
- Threat motives: identifying reasons people might have for targeting your OT for a malicious attack. Motives mostly fall into two categories – intentional and unintentional.
Threats
Understanding the types of events that have the potential to adversely impact your organisation’s OT and ICS is a critical part of cyber risk assessment. These types of threats include analysing the potential of an ‘intrusion’ into your system via a portable device (USB) malicious PDF file, or planting a malicious application, or to observe how your systems work in planning more complex attacks further down the track.
Threat agents
Analysing threat agents means looking at the capacity of internal operators to expose your OT to compromise, as well as external ones.
The Repository of Industrial Security Incidents (RISI) is a database of incidents of a cyber security nature that have (or could have) affected process control, industrial automation or SCADA systems. The data and reports from RISI over many years have suggested the vast majority (80 percent) of breaches are caused unintentionally. Of that number, 48 percent can be traced back to employees, contractors, vendors or industry partners who have access to your ICS.
In other words, you’re more likely to be compromised from inside, so internal should be the starting point, rather than external-based threats.
Threat motives
Like threat agents, analysing threat motives involves looking not only at intentional breaches of your OT but unintended ones too.
Intentional access relates to a third party attempting to access your OT and taking deliberate steps to ensure they have the capability, the resources and a defined objective or outcome they want to achieve from breaking into your system.
Non-intentional threats include accidental software failures and errors in the programming, configuration errors, as well as the architecture and connections to network devices, servers and modules.
The current limitations of risk assessments
While there is data that can be accessed as part of a qualitative analysis of ICS or OT, the data needed to undertake a quantitative analysis is, arguably, in short supply.
Most assessors simply don’t have the data size necessary to properly assess the likelihood of an organisation’s OT being targeted. Then there’s the issue of subjectivity. A malicious actor, for example, might have access to an insider who might have the capability, but has that insider got the intent?
Another limitation is the shortage of experts who know how to accurately simulate cyber-attacks. That’s because cyber criminals do their utmost to avoid attribution. While the 2023 Australian Signals Directorate report makes for sobering reading, it’s likely even the ASD knows very little about the motivations of those who carried out the attacks. Why? Because no one is taking responsibility for the attacks, so there is no transparency.
The sophistication involved in not being caught or having an attack attributed to an individual adversary or team is collectively why cyber security exists: it’s not about the exploitation of one vulnerability; it’s about exploiting many. To pull off an attack like Industroyer 2.0, it’s likely there would have been multiple stages of exploitation to then realise impact. Again, the authorities may never know who’s done it — there is no attribution.
These are the types of challenges that are rarely discussed in risk assessment, and they’re the types of challenges that impede specialists in risk assessment from successfully, and fully, performing their jobs.
How SIS overcomes limitations in risk assessments
It’s important to stress once again: risk assessment seems easy on the outside, but it’s extremely difficult to do well. We’re not saying we’re perfect but, at SIS, we think we offer better outcomes than many because we grasp these limitations and we’ve had years of practice in overcoming them and refining our process.
The ICS Cyber Kill Chain has a significant influence on how we conduct risk assessments. We use real world attacks and frameworks – such as STUXNET, HAVEX, BLACKENERGY2, CRASHOVERRIDE, TRISIS, and Industroyer2, Pipedream – to create modules of the exploitation, simulate it, then relate it back to a client’s infrastructure. This is how we assess the probability and the consequences of that threat being materialised.
We also consider the insider capabilities of performing more basic attacks such as Denial of Service (DoS) attacks, exploitation of unpatched vulnerabilities like privilege escalation exploitation techniques and so on.
Likewise, threat profiling of external threats is a useful strategy. It’s recognised there are cybercrime collectives targeting critical infrastructure. By monitoring those groups, we threat profile an organisation to see if particular groups are targeting a specific industry, including even their country of origin.
The ultimate goal is to give clients visibility into where their OT environment has a cyber threat, and where the best controls can be applied today.
In conculsion
While our experiences in the OT and ICS space tell us no one’s doing risk assessment properly, this is not the fault of risk assessment specialists – it’s simply a fait accompli that needs to be called out and owned, so we can all work to our best within limitations.
Until that happens, risk assessment is a flawed and evolving specialty. And admitting this is not a failing; it’s part of the solution.
Get in touch with one of our specialists if you’d like to find out more about our approach to risk assesments.