In September 2022, the simultaneous hacks of health insurer Medibank Private and telecommunications company Optus served as a wake-up call for many everyday Australians about the reality of cybercrime.
While many organisations in Australia were already focused on cyber security, the hacks reinforced the need to remain vigilant about the processes and practices for protecting their Critical Infrastructure (CI) and Operational Technology (OT) against attacks by hackers.
In November 2023, the Australian Signals Directorate (ASD) Cyber Threat Report 2022-2023 shows that attacks against critical infrastructure and Operating Technology in Australia increased in the previous financial year. Somewhat ironically, this report was released only days after a cyber attack on DP World Australia forced the closure of major Australian shipping ports, grounding 30,000 shipping containers in the process.
In releasing the report, Deputy Prime Minister and Minister for Defence Richard Marles cautioned that “Australian governments, critical infrastructure, businesses and households continue to be the target of malicious cyber actors [and] this report illustrates that both state and non-state actors continue to show the intent and capability to compromise Australia’s networks.”
“The report also confirms that the borderless and multi-billion-dollar cybercrime industry continues to cause significant harm to Australia, with Australians remaining an attractive target for cybercriminal syndicates around the world.”
What the report basically says
Australian networks have been regularly targeted by what the report describes as “both opportunistic and more deliberate malicious cyber activity”, with more than 1,100 cyber security incidents from Australian entities reported to the ASD.
The average cost of cybercrime per reported incident has increased by 14 percent compared to the previous year. Medium-sized businesses in Australia were the hardest hit, with the average cost per incident now sitting at $97,000, while the average cost of cybercrime for a large business is $71,000 and $46,000 per incident for small businesses.
Close to 94,000 reported incidents — a 23 percent increase on the previous 12 months — were made through ReportCyber, equating to approximately one attack reported every six minutes, which is an increase from the previous year’s metric of one every seven minutes.
Calls to the Australian Cyber Security hotline rose by 32 percent, with 33,000 calls received. On average, phone staff took 90 calls per day — an increase from 69 calls per day in the previous reporting period.
Email compromise, business email compromise and online banking fraud were the top three cybercrimes that affected Australian businesses, while identity fraud, online banking fraud and online shopping fraud ranked as the top three types of cybercrimes affecting individuals.
Other key statistics from the 2022-2023 ASD Threat Report include:
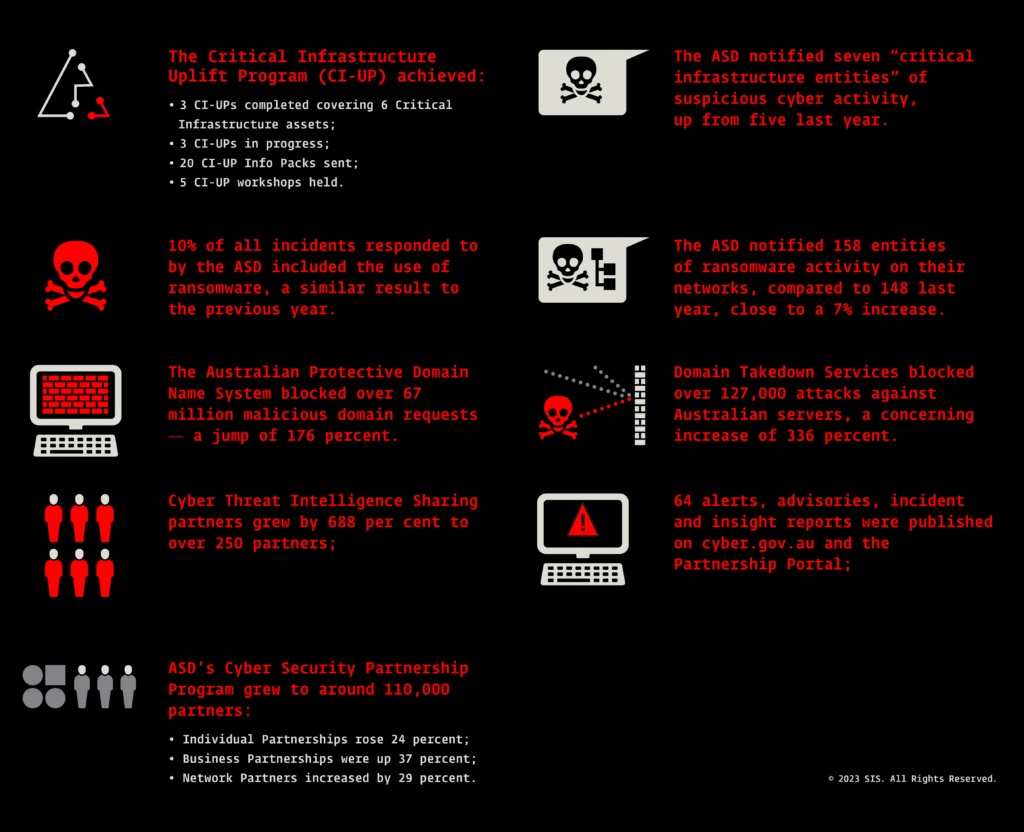
The report identified five key trends:
1. State actors focused on critical infrastructure – data theft and disruption of business.
There were a number of attacks carried out by state-sponsored hackers on critical infrastructure networks run by governments around the world in 2022-2023 – and Australia was no exception.
At the root of these hacks, the ASD says, “networks were targeted by state cyber actors as part of ongoing information-gathering campaigns or disruption activities.” In Australia’s case, they suggest, “the AUKUS partnership, with its focus on nuclear submarines and other advanced military capabilities, is likely a target for state actors looking to steal intellectual property for their own military programs.”
Australia joined governments around the world in calling out Russia and China for their use of state-sponsored cyber-espionage practices to target critical infrastructure in other countries.
2. Australian critical infrastructure was targeted via increasingly interconnected systems
Cloud-hosted systems and other web-based OT were increasingly targeted by hackers and cyber criminals. In 2022-2023, the ASD responded to 143 cyber security incidents on Australian businesses directly related to their operational technology and critical infrastructure networks.
3. Cybercriminals continued to adapt tactics to extract maximum payment from victims
The ASD responded to 127 “extortion-related incidents”, of which 118 “incidents involved ransomware or other forms of restriction to systems, files or accounts.”
Fuelled by a growing network of “access brokers”, ransomware and Denial-of-Service (DoS) attacks were carried out by “hacktivists” on business and individuals have become more sophisticated and lucrative compared to previous years, and this remains a “highly destructive” form of cybercrime.
4. Data breaches impacted many Australians
Closely linked to the abovementioned trend, the ASD report states, “Significant data breaches resulted in millions of Australians having their information stolen and leaked on the dark web — one of many concerns arising from the Medibank Private and Optus data hacks.”
5. One in five critical vulnerabilities were exploited within 48 hours
Despite “patching or mitigation advice being available”, hackers were still able to exploit critical flaws in operating systems and software packages in a relatively short space of time, and initiate what the ASD describes as “significant incidents” and to “compromise networks, aided by inadequate patching”.
What this all means for operational technology
Australian critical infrastructure networks – such as those used in the healthcare sector, food and grocery supply chains and essential services like electricity, gas and water, to name only a few – regularly experienced what it calls “targeted and opportunistic malicious cyber activity”. The report’s authors caution that hacking attempts on critical OT are likely to increase as networks grow in size and “complexity.”
“Malicious cyber actors,” they continue, “can steal or encrypt data, or gain insider knowledge for profit or competitive advantage. Some actors may attempt to degrade or disrupt services and these incidents can have cascading impacts. Designing robust cyber security measures for operational technology environments is vital to protect the safety, availability, integrity and confidentiality of essential services. Secure-by-design and secure‑by-default products should be a priority.”
The report’s authors suggest that businesses and organisations running critical OT need to implement a number of strategies to protect against hackers and cybercriminals. They emphasise the use of industry-best practices, such as the ASD’s Essential 8 framework for risk management, and to regularly scrutinise the organisation’s ICT supply chain for vulnerabilities and risks.
Another important strategy is to thoroughly understand your network. The report recommends organisations to “map [their networks], and maintain an asset registry to help manage devices on all networks, including OT. Consider the security capabilities available on devices as part of routine architecture and asset review, and the most secure approach to hard-coded passwords.”
Other important practices the ASD recommends organisations implement to protect their OT and critical infrastructure include:
- Maintain effective separation between your IT and OT to minimise your attack surface (remote access solutions and third parties within your ICT supply chain):
“OT can be targeted to access a corporate network and vice versa, potentially allowing malicious cyber actors to move laterally through systems to reach their target. Even when OT is not directly targeted, attacks on connected corporate networks can disrupt the operation of critical infrastructure providers.” - “[Prioritising] secure-by-design or secure-by-default products. Consider the security controls of any new software, hardware, or OT before it is purchased, and understand vendor support for future patches and ongoing security costs. Build cyber security costs into budgets for the entire lifecycle of the product, including the product’s replacement.”
- “Understand what is necessary to keep critical services operating and protect these systems as a priority. Ensure OT and IT systems can be, or are, segmented to ensure the service is able to operate during a cyber incident.”
- Follow ASD’s cyber security publications tailored for critical infrastructure entities available at cyber.gov.au.
What industry should take from this
The ASD notes, “To boost cyber security, Australia must consider not only technical controls such as ASD’s Essential Eight, but also growing a positive cyber-secure culture across business and the community. This includes prioritising secure-by-design and secure-by-default products during both development (vendors) and procurement (customers).”
As already outlined, it’s critical your organisation implements a security framework, such as the suggested Essential 8 from the ASD. Internationally recognised best practice standards like IEC 62443 and NIST 800 53 also offer good protocols. But if you’re not in the cyber security business, how do you go about effectively implementing these frameworks?
Maximising the benefits of security frameworks are not easy for organisations to handle internally. When looking to apply them, the most effective and economical decision is likely to partner with a professional security consulting organisation and let them apply their specialist knowledge to your situation.
Finally, the ASD emphasise their own programs for supporting critical infrastructure and OT. Initiatives like the Cyber Uplift Program and what they describe in the report as “cyber threat intelligence sharing” are helpful and cost-effective ways of protecting your organisation, employees and the community from cyber criminals and hackers today against an incident that will not possibly happen but most certainly will.
Find out how SIS can implement an OT security framework for your organisation.