It’s likely you’ve given some thought, maybe even a lot, to your company’s cyber security requirements. You may have researched what others are doing across industry, performed a risk assessment of sorts and put some new security measures in place. As far as you’re concerned, you’re keeping up with ever-evolving threats and making the grade.
But here lies the problem: the generally accepted approach to cyber security just won’t cut it when it comes to your industrial assets.
While you’re going about your business believing your assets are secure, you could actually be highly vulnerable and, to be honest, a metaphorical sitting duck just waiting for a cyber attack to occur. This exploitation may not just impact your Information Technology (IT) – company emails, personal records, documentation and so on – it may penetrate even deeper; at the highly sensitive core of your production environment; your Operational Technology (OT).
In Australia, Home Affairs Minister Peter Dutton has warned of prolonged and catastrophic cyber-attacks on critical infrastructure that could disrupt entire industries. His concern has been specifically directed at Australia’s energy sector and the possibility of widespread failure of electricity networks, with a flow-on effect of potentially disrupting hospitals, transport, banking and food supplies. His warning comes off the back of recent incidents targeting global multinational energy groups.
Research conducted by IBM showed Operational Technology incidents had risen by 2,000 percent in 2019. Such an alarmingly high percentage suggests there is something critically wrong with the generally accepted approach to OT cyber security internationally.
This needs to change.
Speaking at the Cyber Security for Critical Assets virtual Industrial Cyber Security Summit USA in October 2020, Rob Dyson from IBM said, “Security awareness within OT environments is very low. This is an area where the employees, contractors, vendors did not have to think about cyber security years ago, but today they do.”
“There’s often very good physical security but very limited cyber security,” he continued. “All the experts are typically over in the corporate IT security team and very limited OT security professionals are available to work in the OT environment, and those security professionals in the corporate side don’t understand the OT environment. So, you really have a disparate situation where you need to cross-train or find people who are skilled in the area of OT.”
To highlight Rob Dyson’s point, let’s look at the following visual representation of an organisational functional hierarchy model (see below).
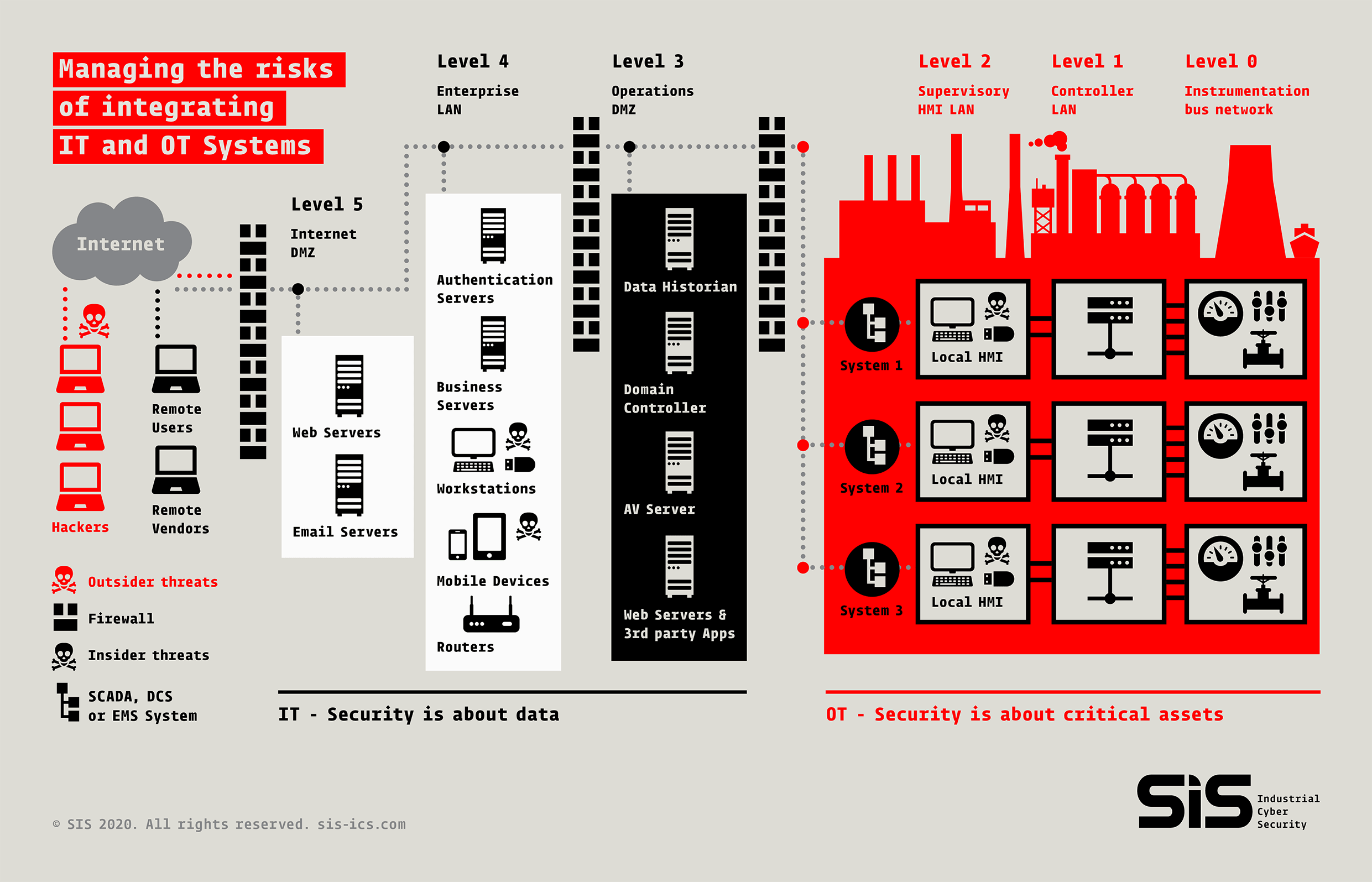
You’ll note that Levels 5, 4 and 3 in this diagram represent where IT assets typically reside. When considering cyber security, assessing risk and then implementing security controls, it is these three levels where most businesses will direct their focus (the front door). Unfortunately, that means Levels 2, 1 and 0 – the levels where operational technology lies – are effectively left with the back door wide open.
As Dyson explains, this oversight in OT network security largely occurs because those employed as IT security experts simply do not have the engineering knowledge or skills to properly address OT assets. This is not so much a failure in individual people but a failure of the industry in general for not keeping up with the advances of those who seek to disrupt and even destruct your critical assets for either economic gain or espionage.
When you think of cyber attacks, it’s likely you’ll think of the financial losses and a possible dent in your brand or company reputation. But an attack on your OT environment could have even more serious and wide-ranging implications including outages of critical services, environmental damage and, ultimately, potential loss of human life.
Governments and critical infrastructure owners and operators are waking up to the need for greater sophistication in cyber security, especially when it comes to protecting a company’s all-important operational technology. The fact that this article has been written is proof such issues are being aired and addressed, with a movement towards recognising the talents of established industrial cyber security experts, and the training of more, to fill a very real hole.
It is clear that focusing on the security of IT assets alone, does not address the very real need to protect critical OT assets. Tactical point solutions will not do. Industry needs to adopt a strategic approach to industrial cyber security.
In the meantime, if you’re taking a copy-cat approach to security, you’re not doing yourself any favours. Every OT environment is different. You’re best to regard any actions your contemporaries are taking as potentially insufficient for your own requirements. That may sound cynical but it’s more than likely to be true.
Set a new standard for others to follow. Set a budget to build an industrial cyber security strategy that is specific to your requirements using a proven methodology. Open your mind to think holistically about cyber security and seek out qualified specialists to help guide you and make it happen.
You simply cannot afford not to invest properly in safeguarding your OT assets. It could be the single most important thing you do for your organisation.
Want to secure your OT before it’s too late? Talk to one of our elite industrial cyber security specialists.