Approach
We use bespoke methodologies that are systematic and specific to Operational Technology (ICS/SCADA) to combat the ever-evolving threat of attack.
Our suite of services cover the full threat lifecycle of industrial cyber security, from assessment to incident response.
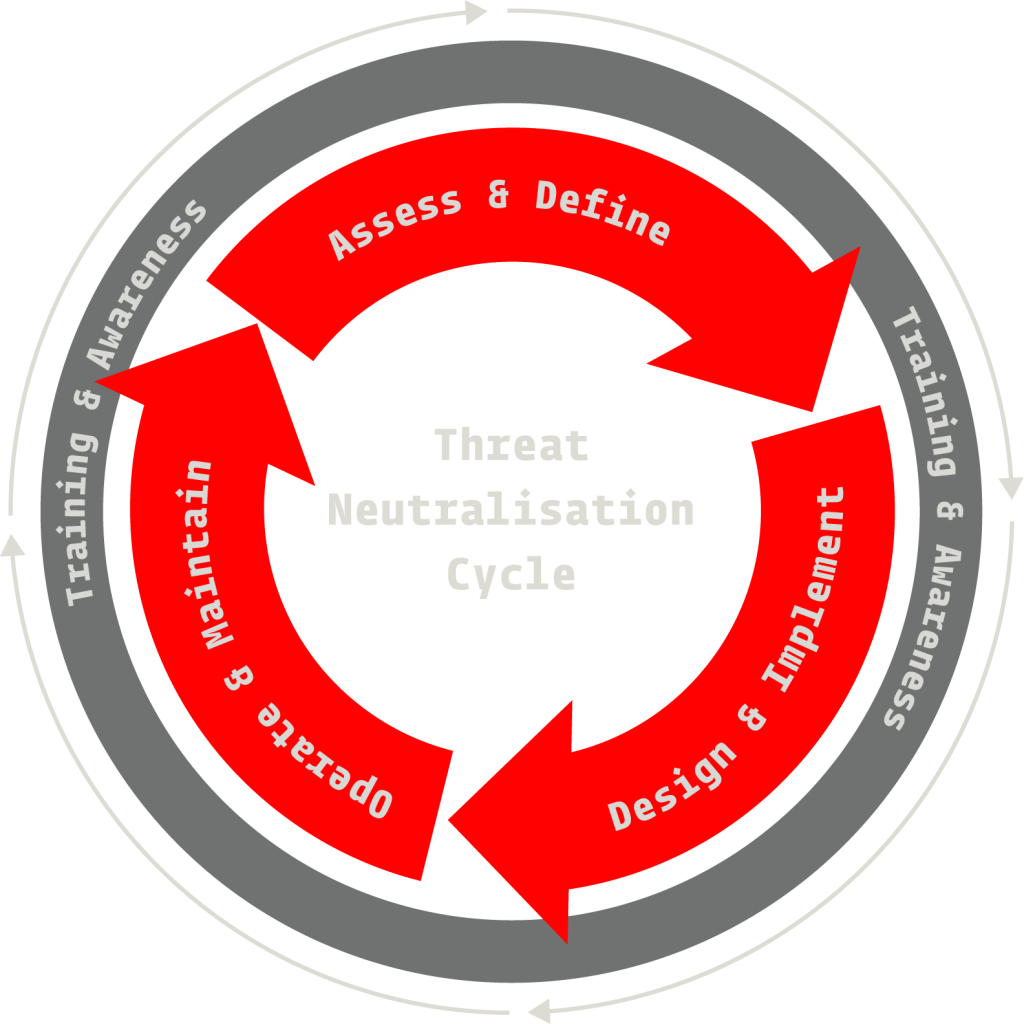
Assess & Define
We help you to assess your critical systems, processes and procedures, to identify vulnerabilities and gaps when benchmarked to industry standards, for risk mitigation.
Our services include:
- Site survey and asset inventorying
- Technical vulnerability assessment & security testing (pen-testing), including red-teaming
- Threat and risk assessment
- Health check, gap analysis and maturity assessments, benchmarked to leading industrial cyber security standards
Design & Implement
We use a proven methodology to design secure architectures for your plant. Our specialists install and configure your security products and technologies.
Our services include:
- Establishment of cyber security requirement specifications
- Design of security architecture
- Security zone and conduit modelling constructs
- Design of infrastructure layouts and security platforms
- Design of implementation plans and transition-state architectures
- Test plan (FAT and SAT) development & execution
- Installation and configuration of security products and technologies
Operate & Maintain
We help you to define the operational requirements to maintain key security services such as security monitoring, patch management, change management, backup and recovery procedures. Such operational activities form the key pillar of your Cyber Security Management System (CSMS).
Our services include:
- Development of Cyber Security Management Systems
- Security monitoring managed services
- Incident response managed services
- Vulnerability / patch management managed services
- Cyber forensics
- Audit and compliance assessments
- Device robustness testing and assurance

SIS OT Security Operations Centre
Our OT SOC is a cost-effective outsourced service that delivers managed OT security with real-time monitoring, analytics and reporting by an elite team of industrial cyber security specialists.
- One of the world’s first 100% dedicated OT SOCs
- Average cost efficiencies of 80%, compared to an internal SOC model
- 24×7 OT monitoring by a specialist team
- Powered to inspect deep inside OT networks
Training & Awareness
Our specialised industrial cyber security training covers all elements of the threat neutralisation cycle, and how to manage specific cyber threats to your industrial assets.
Our training includes:
- Certified Industrial Cyber Security Specialist (CICSS) course
- Onsite tailored, organisation-wide training
- Incident simulations and drill facilitation
- Red vs Blue team events