Managed Services
Managed OT cyber
security with real-time
detection and response
-
One of the world’s first, 100% dedicated,
OT-SOCs - Instantly boost your cyber capability by accessing a mature OT-SOC
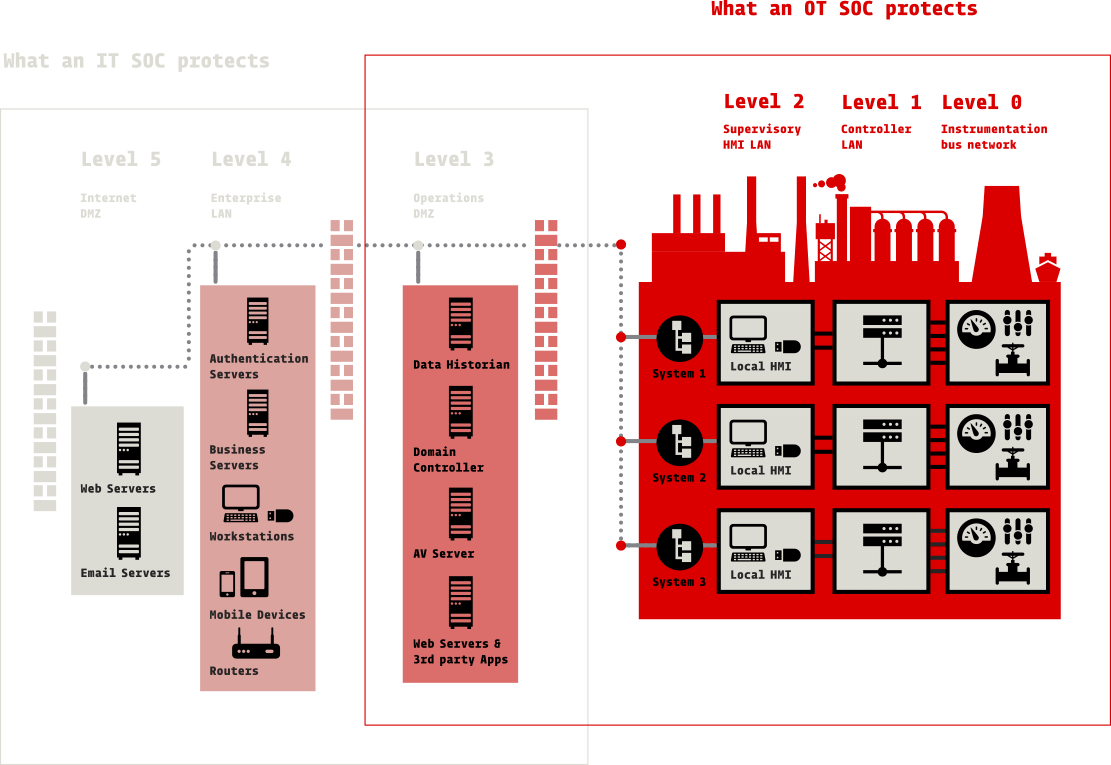
- 24/7 visibility of threats targeting OT assets
- Live monitoring by an elite team of industrial cyber security specialists, capability difficult to replicate in-house
- Predictable fixed pricing, per agent/node
inside your network?
The threat landscape is constantly changing, while at the same time digital devices and cloud computing mean that everything is more connected than ever. This has created a challenge for operators of industrial networks and critical infrastructure to maintain the right skills and knowledge to respond to cyber attacks effectively.
To have a totally resilient OT network, you need 24/7 monitoring to detect and respond to potential cyber threats. This means a dedicated OT-SOC is vital to any industrial organisation’s cyber security game plan.
Why a dedicated OT-SOC? Because IT & OT operate in different environments, serve different purposes and have their own unique requirements. They also require specialists with different skill sets.
The only way to effectively neutralise the threat in industrial environments is with OT security specialists.
Our recommended approach is to manage your OT-SOC remotely by collecting and analysing your data on the dedicated SIS OT-SOC platform.
This is the most cost and time-effective solution for an OT-SOC, giving you immediate access to a mature and established environment.
An off-premises approach also future-proofs your OT environment, with scalability and flexibility to easily expand across multiple sites and locations.

In situations where organisations need to maintain and comply with local data sovereignty requirements, we manage your in-house OT-SOC via Remote Access.
Tap into external specialist knowledge and capability to set up a new platform or to more effectively use your existing platform for detection and response.
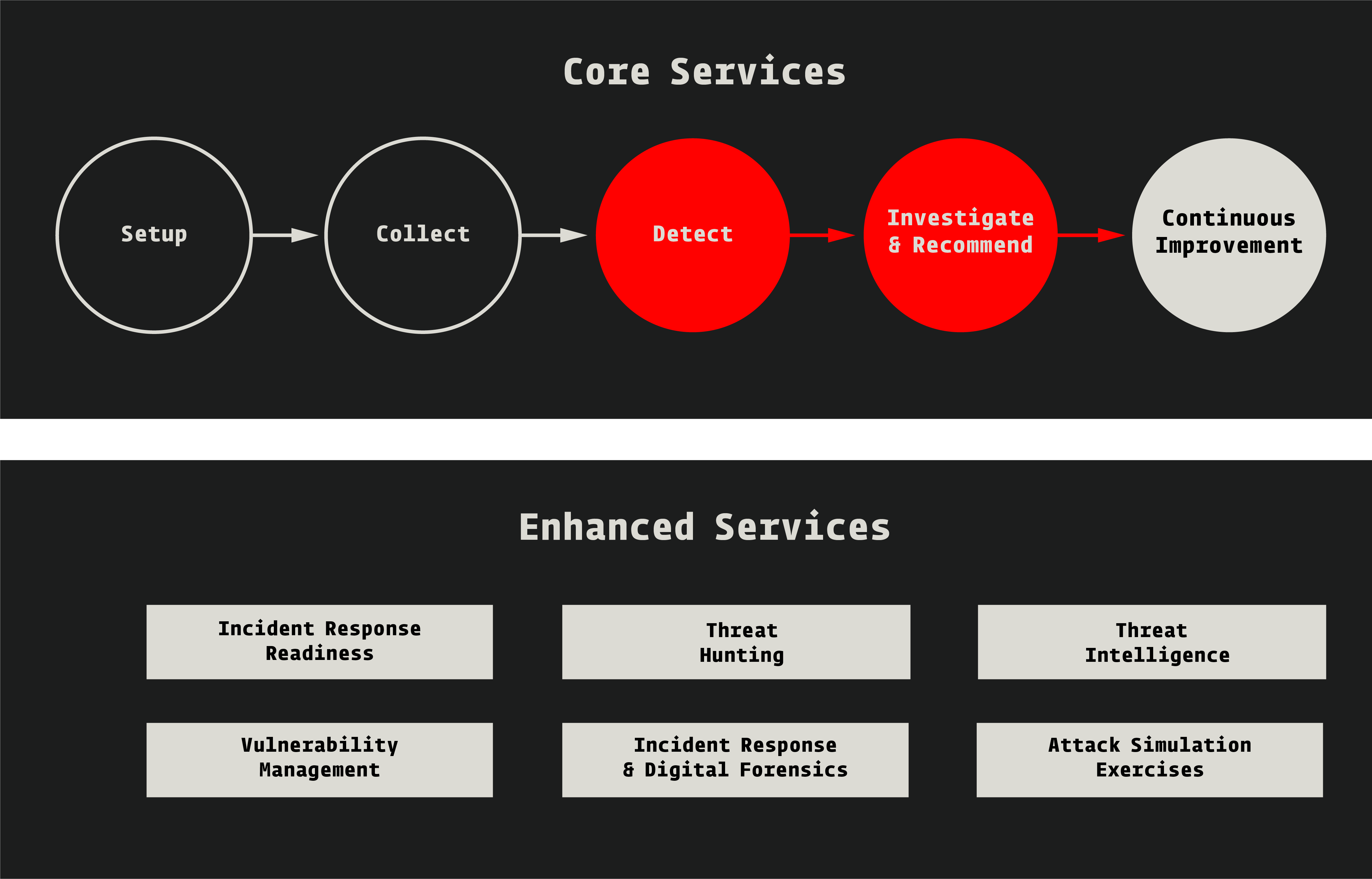
The Core Services of our OT-SOC cover the full threat life-cycle.
Setup
Reviewing of infrastructure. Determine business objectives, critical assets and identify integration points with existing services. Develop and validate threat and use cases specific to your organisation.
Investigate & Recommend
Alert triage and initial assessment of security events then remediation actions for real security incidents including on-call support when required.
Collect
Setup and deploy the OT-SOC systems, agents and components for the collection of event information.
Continuous Improvement
OT network behavioural learning and fine-tuning of detection rules to align with your unique environment.
Detect
Monitoring and reviewing events and alerts against your organisation's architecture provides a unique view into threats based on the systems under consideration.
In addition to our core services we offer a suite of Enhanced Services to further strengthen your defences.
Incident Response Readiness
Be fully prepared to respond to an incident, then contain, eradicate and recover from an attack.
Incident Response & Digital Forensics
Our elite team of specialists respond to security incidents with speed and precision to minimise data loss, production downtime and disruption to operations.
Vulnerability Management
Take a proactive approach to identifying and mitigating the potential vulnerabilities impacting your organisation’s security.
Threat Intelligence
Create a threat profile of your organisation with actionable threat intel based on strategic, tactical and operational threat feeds to aid analysts in security investigations and response actions.
Threat Hunting
Develop a tailor made threat hunting program for your organisation based on MITRE ATT&CK for ICS Framework.
Attack Simulation
Drills and exercises that measure detection maturity and capability, increase vigilance and improve your security posture.
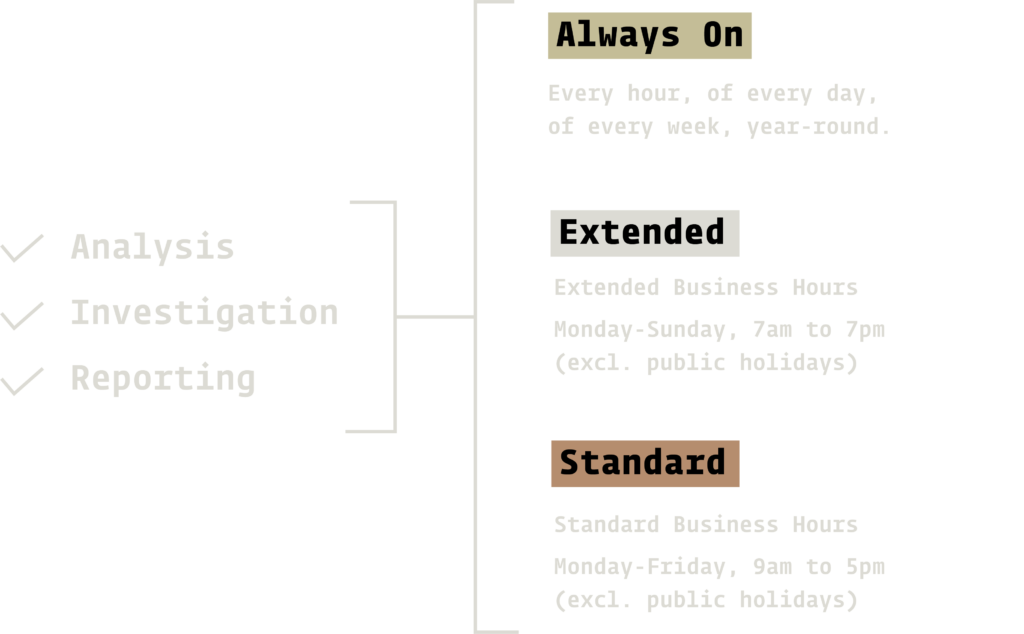
SIS’ OT-SOC monitors and detects security events 24 hours a day, year-round.
Our 3 tiers of service provide you with OT-SOC Analyst availability, based on your specific needs.
Set up a meeting with an SIS specialist
Find out more and connect
with a specialist from our team
advice specific to your operating conditions.
Neutralising
the Threat
Protect your critical assets from the threat of cyber attack.
Get in touch with our industrial cyber security specialists.